Why print?
Printing Solutions: Is printing still necessary these days? Digital transformation continues to progress and affects companies in all industries.…




















Your redIT team
“We accompany our customers on their digital journey and profitably bring in our profound knowledge as an IT partner about business relationships as well as our many years of experience.”
Gerhard Nigg, Head of Business Solutions

«Cloud solutions are one of the basic requirements for digital transformation. As digitalization experts, we bring the cloud into your company.»
Yves Monbaron, Head of Cloud Solutions

«As an IT partner, we have experience in different industries. In order to meet the challenge of digitalization, we offer optimized solutions for various industries – standardization as far as possible, specialization where necessary.”
Daniel Merz, Head of Sales & Marketing
«Digitalization is changing the way companies organize their work processes. New business models are emerging, value chains are changing and innovation cycles are accelerating. As digitalization experts, we want to support you on this path.”
Andrew Kleeb

Your redIT team
“We accompany our customers on their digital journey and profitably bring in our profound knowledge as an IT partner about business relationships as well as our many years of experience.”
Gerhard Nigg, Head of Business Solutions

«Cloud solutions are one of the basic requirements for digital transformation. As digitalization experts, we bring the cloud into your company.»
Yves Monbaron, Head of Cloud Solutions

«As an IT partner, we have experience in different industries. In order to meet the challenge of digitalization, we offer optimized solutions for various industries – standardization as far as possible, specialization where necessary.”
Daniel Merz, Head of Sales & Marketing

«Digitalization is changing the way companies organize their work processes. New business models are emerging, value chains are changing and innovation cycles are accelerating. As digitalization experts, we want to support you on this path.”
Andrew Kleeb

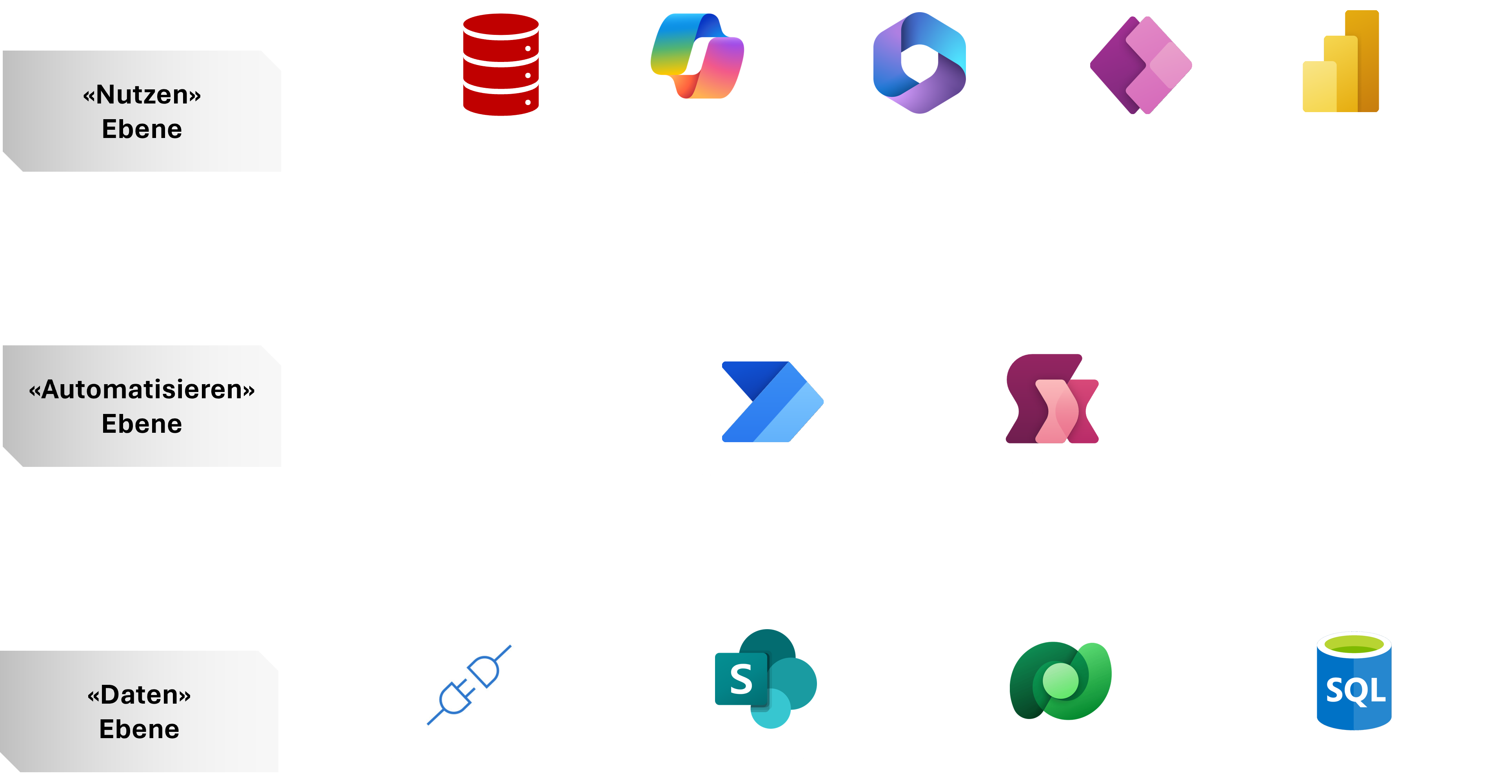
More productivity with M365 & Power Platform
Would you like to increase your productivity and promote efficient work in your company? Our productivity assessment shows you how effectively you are using the tools available. Try our free demo to learn more.
Printing Solutions: Is printing still necessary these days? Digital transformation continues to progress and affects companies in all industries.…
What's new in Microsoft Teams? Good teamwork is crucial for successful work. Microsoft Teams offers the ideal…
redIT Insights – CloudFest, Easter Brunch & E-Cars We at redIT have experienced a lot in the last few weeks and give you...

Sananet AG
Successful into the future with digital processes
Digital processes and highly flexible IT ensure that Sananet can react quickly to changes.

H Focus AG
Unlimited mobile with Office 365 and Microsoft Teams
For H Focus, it is crucial to have secure access to data and systems at any time, from anywhere.

Regionalwerke Baden AG
Intelligent IT platform for more efficiency in maintenance
The new IT platform ensures high availability, maximum security and more efficiency in operations/maintenance at RWB.




















